NBTscan
NBTscan Description
NBTscan is a program for scanning IP networks for NetBIOS name information. It sends NetBIOS status query to each address in supplied range and lists received information in human readable form. For each responded host it lists IP address, NetBIOS computer name, logged-in user name and MAC address (such as Ethernet).
GitHub: https://github.com/resurrecting-open-source-projects/nbtscan
Author: Alla Bezroutchko, Resurrecting Open Source Projects
License: GPLv2
NBTscan Help
Usage:
nbtscan [-v] [-d] [-e] [-l] [-t TIMEOUT] [-b BANDWIDTH] [-r] [-q] [-s SEPARATOR] [-m RETRANSMITS] (-f FILENAME)|(IP_OR_RANGE)
Options:
-v verbose output. Print all names received from each host -d dump packets. Print whole packet contents. -e Format output in /etc/hosts format. -l Format output in lmhosts format. Cannot be used with -v, -s or -h options. -t timeout wait timeout milliseconds for response. Default 1000. -b bandwidth Output throttling. Slow down output so that it uses no more that bandwidth bps. Useful on slow links, so that ougoing queries don't get dropped. -r use local port 137 for scans. Win95 boxes respond to this only. You need to be root to use this option on Unix. -q Suppress banners and error messages, -s separator Script-friendly output. Don't print column and record headers, separate fields with separator. -h Print human-readable names for services. Can only be used with -v option. -m retransmits Number of retransmits. Default 0. -f filename Take IP addresses to scan from file filename. -f - makes nbtscan take IP addresses from stdin. <scan_range> what to scan. Can either be single IP like 192.168.1.1 or range of addresses in one of two forms: xxx.xxx.xxx.xxx/xx or xxx.xxx.xxx.xxx-xxx.
You have to supply at least one argument, the address range, in one of three forms:
- xxx.xxx.xxx.xxx
Single IP in dotted-decimal notation. Example: 192.168.1.1
- xxx.xxx.xxx.xxx/xx
Net address and subnet mask. Example: 192.168.1.0/24
- xxx.xxx.xxx.xxx-xxx
Address range. Example: 192.168.1.1-127. This will scan all addresses from 192.168.1.1 to 192.168.1.127
Understanding NBTscan Output
NBTscan produces a report like that:
IP address NetBIOS Name Server User MAC address ----------------------------------------------------------------------- 192.168.1.2 MYCOMPUTER JDOE 00-a0-c9-12-34-56 192.168.1.5 WIN98COMP <server> RROE 00-a0-c9-78-90-00 192.168.1.123 DPTSERVER <server> ADMINISTRATOR 08-00-09-12-34-56
First column lists IP address of responded host.
Second column is computer name.
The third column indicates whether the system uses (or can use) shared resources such as Share folders (network folders) or printers. If the third field is <server>, it does not necessarily mean that this computer is running Windows Server. This means that services are running on this system that allow you to find this computer on the local network, and folder and/or printer sharing is enabled. That is, the computer can act as a server for sharing files and printing over the network.
The fourth column shows the username. If no one is logged on from this computer, this is the same name as the computer name. For modern operating systems, the tool usually cannot determine the username, so it will most likely be written <unknown> there.
Last column shows adapter MAC address.
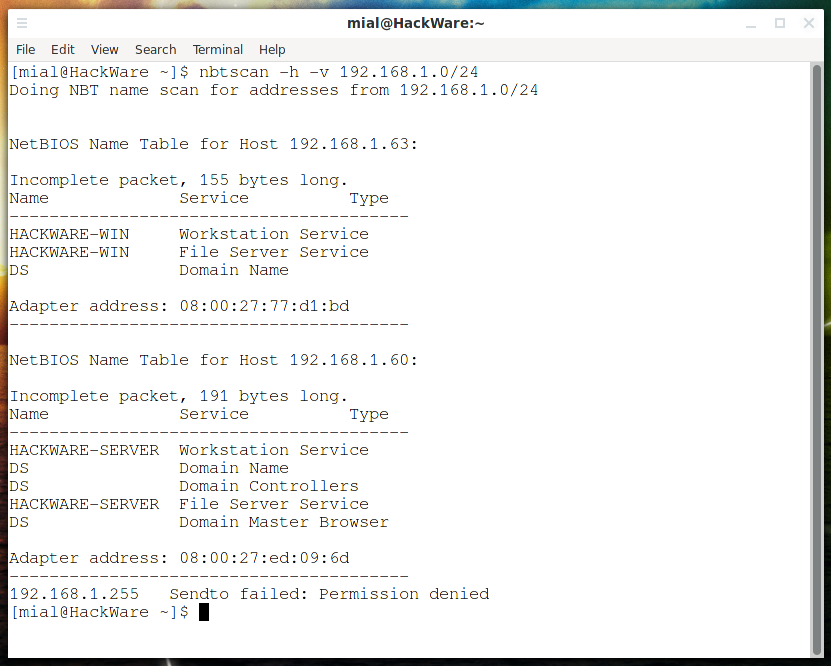
If run with -v switch NBTscan lists whole NetBIOS name table for each responded address. The output looks like that:
NetBIOS Name Table for Host 192.168.1.123:
Name Service Type
----------------------------------------
DPTSERVER <00> UNIQUE
DPTSERVER <20> UNIQUE
DEPARTMENT <00> GROUP
DEPARTMENT <1c> GROUP
DEPARTMENT <1b> UNIQUE
DEPARTMENT <1e> GROUP
DPTSERVER <03> UNIQUE
DEPARTMENT <1d> UNIQUE
??__MSBROWSE__? <01> GROUP
INet~Services <1c> GROUP
IS~DPTSERVER <00> UNIQUE
DPTSERVER <01> UNIQUE
Adapter address: 00-a0-c9-12-34-56
----------------------------------------
NetBIOS Suffix
NetBIOS Suffix, aka NetBIOS End Character (endchar), indicates service type for the registered name. The most known codes are listed below. (U = Unique Name, G = Group Name)
Name Number(h) Type Usage
--------------------------------------------------------------------------
<computername> 00 U Workstation Service
<computername> 01 U Messenger Service
<\--__MSBROWSE__> 01 G Master Browser
<computername> 03 U Messenger Service
<computername> 06 U RAS Server Service
<computername> 1F U NetDDE Service
<computername> 20 U File Server Service
<computername> 21 U RAS Client Service
<computername> 22 U Exchange Interchange(MSMail Connector)
<computername> 23 U Exchange Store
<computername> 24 U Exchange Directory
<computername> 30 U Modem Sharing Server Service
<computername> 31 U Modem Sharing Client Service
<computername> 43 U SMS Clients Remote Control
<computername> 44 U SMS Administrators Remote Control Tool
<computername> 45 U SMS Clients Remote Chat
<computername> 46 U SMS Clients Remote Transfer
<computername> 87 U Microsoft Exchange MTA
<computername> 6A U Microsoft Exchange IMC
<computername> BE U Network Monitor Agent
<computername> BF U Network Monitor Application
<username> 03 U Messenger Service
<domain> 00 G Domain Name
<domain> 1B U Domain Master Browser
<domain> 1C G Domain Controllers
<domain> 1D U Master Browser
<domain> 1E G Browser Service Elections
<INet~Services> 1C G IIS
<IS~computer name> 00 U IIS
FAQ
1. Q: NBTscan lists my Windows boxes just fine but does not list my Unixes or routers. Why?
A: That is the way it is supposed to work. NBTscan uses NetBIOS for scanning and NetBIOS is only implemented by Windows (and some software on Unix such as Samba).
2. Q: Why do I get "Connection reset by peer" errors on Windows 2000?
A: NBTscan uses port 137 UDP for sending queries. If the port is closed on destination host destination will reply with ICMP "Port unreachable" message. Most operating system will ignore this message. Windows 2000 reports it to the application as "Connection reset by peer" error. Just ignore it.
3. Q: Why NBTscan doesn't scan for shares? Are you going to add share scanning to NBTscan?
A: No. NBTscan uses UDP for what it does. That makes it very fast. Share scanning requires TCP. For one thing, it will make nbtscan more slow. Also adding share scanning means adding a lot of new code to nbtscan. There is a lot of good share scanners around, so there is no reason to duplicate that work.
4. Q: Why do I get 00-00-00-00-00-00 instead of MAC address when I scan a Samba box?
A: Because that's what Samba send in response to the query. Nbtscan just prints out what it gets.
NBTscan Usage Example
Scans the whole 192.168.1.0/24 network:
nbtscan -r 192.168.1.0/24
Scans a range from 192.168.1.25 to 192.168.1.137:
nbtscan 192.168.1.25-137
Scans C-class network. Prints results in script-friendly format using colon as field separator:
nbtscan -v -s : 192.168.1.0/24
Produces output like that:
192.168.0.1:NT_SERVER:00U 192.168.0.1:MY_DOMAIN:00G 192.168.0.1:ADMINISTRATOR:03U 192.168.0.2:OTHER_BOX:00U ...
Scans IP addresses specified in file iplist.txt:
nbtscan -f iplist.txt
Scans the whole 192.168.1.0/24 subnet, list all names received from each host (-v), print human-readable service names (-h):
nbtscan -h -v 192.168.1.0/24
How to install NBTscan
Installation on Kali Linux
sudo apt install nbtscan
Installation on Debian, Linux Mint, Ubuntu
sudo apt update sudo apt install nbtscan
Installation on BlackArch
The program is pre-installed on BlackArch. To install in minimal builds run:
sudo pacman -S nbtscan
NBTscan Screenshots
NBTscan Tutorials
- NetBIOS: what it is, how it works and how to use in information security
- Online service: NetBIOS, SMB (NetBIOS) and Samba (Linux) scanner
Related tools
- NetBIOS Share Scanner (100%)
- NMBscan (100%)
- nbtscan-unixwiz (100%)
- DNSRecon (68.6%)
- mat2 (68.6%)
- Maltego (RANDOM - 62.9%)

Comments are Closed