nbtscan-unixwiz
nbtscan-unixwiz Description
This is a command line tool that scans for open NETBIOS name servers on a local or remote TCP/IP network, the first step in finding open shares. It is based on the functionality of the standard Windows nbtstat tool, but it can work not only with a single address, but also with a range of addresses.
The tool has a version for Windows and Linux.
The Win32 version runs on Windows since Windows 9x, NT and 2000 and later, available below as nbtscan.exe. It is written in portable C and is less than 40 KB, it does not require special libraries or DLLs, and runs in an MS-DOS command window.
The Linux version has no dependencies and works on all distributions.
Homepage: http://unixwiz.net/tools/nbtscan.html
Author: Steve Friedl
License: public domain
nbtscan-unixwiz Help
Usage:
nbtscan-unixwiz [options] target [targets...]
Targets are lists of IP addresses, DNS names, or address ranges. Ranges can be in /nbits notation ("192.168.12.0/24") or with a range in the last octet ("192.168.12.64-97")
Option:
-V show Version information -f show Full NBT resource record responses (recommended) -H generate HTTP headers -v turn on more Verbose debugging -n No looking up inverse names of IP addresses responding -p <n> bind to UDP Port <n> (default=0) -m include MAC address in response (implied by '-f') -T <n> Timeout the no-responses in <n> seconds (default=2 secs) -w <n> Wait <n> msecs after each write (default=10 ms) -t <n> Try each address <n> tries (default=1) -P generate results in perl hashref format
Understanding NETBIOS
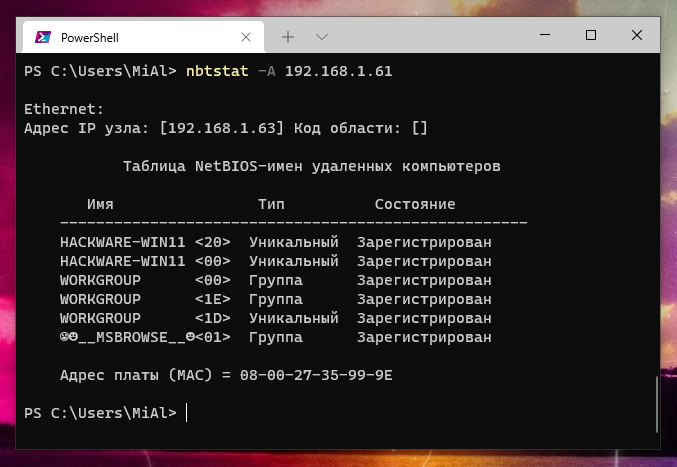
NETBIOS is commonly known as the Windows "Network Neighborhood" protocol, and (among other things), it provides a nameservice that listens on UDP port 137. When it receives a query on this port, it responds with a list of all services it offers. Windows ships with a standard tool nbtstat which queries a single IP address when given the -A parameter. When run against a machine on the local network (a development box), it shows:
nbtstat -A 192.168.1.99
Output example:
NetBIOS Remote Machine Name Table
Name Type Status
---------------------------------------------
XPDEV <00> UNIQUE Registered
UNIXWIX <00> GROUP Registered
XPDEV <03> UNIQUE Registered
XPDEV <20> UNIQUE Registered
UNIXWIX <1E> GROUP Registered
MAC Address = 00-50-04-6D-50-37
The numeric code (in hexadecimal) and the Type serve to identify the service being offered, and (for instance) a UNIQUE code of <20> indicates that the machine is running the file-sharing service. Unfortunately, nbtstat only reports the codes, and it requires looking up the meanings elsewhere. The References section at the end of this document lists some resources to learn what all the codes mean.
Machines participating in NETBIOS listen on UDP port 137 for these queries and respond accordingly. Simple configurations might only have a few resource records (as above), but an NT server supporting a large enterprise could easily have more than a dozen. Though it's sometimes useful to examine the full set of resource records for a given machine, in practice it's more useful to summarize them into the key "interesting" services.
Our tool has taken this approach. Not only does it scan ranges of addresses -- instead of just one machine -- but it can fully decode most of the resource record types and can summarize the interesting data on a one-line display.
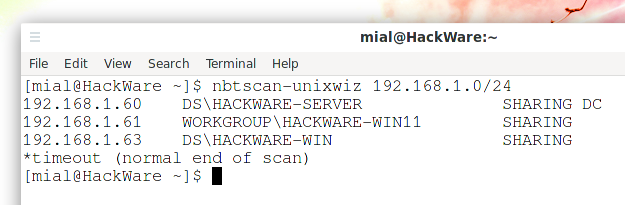
On our network we have quite a few machines, but it appears that only three respond to our queries:
nbtscan 192.168.1.0/24
Output example:
192.168.1.3 MTNDEW\WINDEV SHARING DC 192.168.1.5 MTNDEW\TESTING 192.168.1.9 MTNDEW\WIZ SHARING U=STEVE 192.168.1.99 MTNDEW\XPDEV SHARING
The first column is the IP address, then the NT domain and machine name, followed by the list of "interesting" services about each one. In many cases, the summary information is based on guesses, observations, and highly incomplete information, and we invite submissions by others who can help us pinpoint more entries like this.
| Token | Meaning |
|---|---|
| SHARING | The machine in question is running the file and print sharing service, but this does not necessarily mean any shares are published or that we'll be able to see any of them. Actual enumeration of the shares is done via a different mechanism outside the scope of this program. |
| DC | This machine appears to be a Windows NT domain controller, either primary or secondary. |
| U=user | This machine appears to have a logged-in user with the name indicated. This is often only a guess, and it's common for our algorithms to miss a valid user (especially if the user name is the same as the machine name). |
| IIS | This machine appears to have Microsoft's Internet Information Server (IIS) installed, though we believe that there are related tools that can cause this to appear as well. It doesn't necessarily mean that IIS is actually running. |
| EXCHANGE | This machine appears to be running Microsoft Exchange. |
| NOTES | This machine appears to be running Lotus Notes |
| ? | This means that the remote is advertising a NETBIOS resource record that we don't understand, and it can prompt us to run the scan again with the -f option and research it: we hope to use this feedback to make the program smarter in the future. |
Specifying target ranges
The target can be designated by either an IP address or a hostname. You can specify one or more targets, separated by spaces. Each target will be tested in turn. If any IP address is written incorrectly, or if it was not possible to resolve the domain name to IP, then this is a fatal error. If any IP address is mentioned more than once, then this is not an error, although it is meaningless.
To scan a range of addresses, use the CIDR notation NETWORK/BITS, for example, 192.168.7.0/24. Traditionally, the slash notation requires the "base" address to be at the beginning of a given range, but this tool determines the beginning of the range automatically, so any address will do.
When scanning a remote network denoted by CIDR notation, the tool excludes the first and last addresses in the range that would otherwise be implied by the netmask. This is because the first and last addresses are usually reserved for translation to the local network segment. For example, when considering 10.1.1.0/24, addresses 10.1.1.0 and 10.1.1.255 are not scanned. To change this, the double-slash //BIT notation can be used to include every address within the range, including intended broadcast addresses, and this should be used when the remote netmask is unknown. Example: 10.1.1.32//29 or www.unixwiz.net//27.
In addition to the /BIT notation, targets may be specified with a "range" notation in the last octet. This can be used to specify a range that does not match the standard subnet, such as 10.1.1.17-93. The range notation is not compatible with CIDR notation and cannot be used with a hostname.
Command Line Parameters
When nbtscan is run without command-line arguments, it reports a short "help" listing that summarizes the options available, which are expanded on here.
--version
-V
This simply shows the current version information, and I try to keep it updated on each rebuild. Version history is below.
-f
This shows the full NBT resource record responses for each machine scanned, not just the one-line summary. This is recommended when studying one single machine, but it's much less useful when scanning a larger range.
-O outfile
Send results to outfile rather than to the standard output.
-H
Generate an HTTP header. During penetration testing, sometimes we are able to install the nbtscan.exe program on a remote IIS web server and run it with the "Unicode" exploit, but since the output is "regular" text, the output gets confused by the web server that thinks it's a broken CGI script. The -H option addes a simple Content-type: text/plain header with a blank line that makes the output show up correctly.
-P
Generate Perl hashref output, which can be loaded into an existing program for easier processing. This is much easier than parsing text output.
-v
This turns on some more verbose debugging, but this is really only meant for the developer's use and probably won't help an end-user that much. The code considered "verbose" changes from release to release as bugs are tracked down, and we make no effort to make this useful in the general case.
-n
In a few reporting modes, the IP address of the remote machine is used as a key to look up the "inverse" name. This is normally helpful, but many nameservers are misconfigured in a way that make this appear to "hang", so -n turns off this inverse name lookup.
-p port
This allows specification of a UDP port number to be used as the source in sending a query. Normally the program picks a random ephemeral port number, and this is entirely sufficient in most cases.
But some Windows 95 machines send their responses to port 137 no matter where the query came from (we consider this a bug), so using -p 137 will force nbtscan to bind to this port instead of the random one. In addition, some older versions of the ZoneAlarm personal firewall would incorrectly allow NETBIOS queries if the source port is 53 (DNS).
But note that you can't bind to a port that already is in use, and on Windows this usually means that port 137 is unavailable to you.
-m
Include the MAC (aka "Ethernet") addresses in the response, which is already implied by the -f option.
-T secs
When scanning a large range of addresses, it's not always clear when we are "finished". If we send out (say) five queries, we're clearly done when we get five responses, but if any machine does not respond, we have to rely on timeouts. The -T option controls how long we'll wait for any response, and the default is 2 seconds.
-w msecs
Unless the local network is being scanned, we cannot typically blast many queries lest packets be lost on the way. We normally pause for a short time after each network write operation to allow things to clear out before sending another, and this allows the "tuning" of that time. It is specified in milliseconds, and the default is 10 milliseconds.
-t tries
Try each address up to tries times, which is useful when dealing with a remote network that is (somehow) dropping packets. Once a given machine has responded, it won't be queried again. Default = 1.
-n
Don't look up inverse DNS names in the full listing (show IP addresses).
-1
Force the use of Winsock version 1 (Windows only) rather than the default which is usually version 2.
nbtscan-unixwiz Usage Example
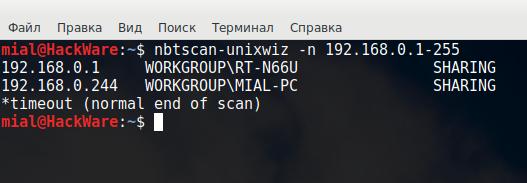
Scan a range of IP addresses (192.168.0.100-110) without performing reverse name resolutions (-n):
nbtscan-unixwiz -n 192.168.0.100-110
Output example:
192.168.0.105 WORKGROUP\RETROPIE SHARING *timeout (normal end of scan)
Scan a single IP address (192.168.0.38) and show the full NBT resource record responses for each machine scanned (-f):
nbtscan-unixwiz -f 192.168.0.38
Output example:
192.168.0.38 WORKGROUP\DOOKOSSEL SHARING DOOKOSSEL <00> UNIQUE Workstation Service DOOKOSSEL <03> UNIQUE Messenger Service<3> DOOKOSSEL <20> UNIQUE File Server Service ..__MSBROWSE__.<01> GROUP Master Browser WORKGROUP <00> GROUP Domain Name WORKGROUP <1d> UNIQUE Master Browser WORKGROUP <1e> GROUP Browser Service Elections 00:00:00:00:00:00 ETHER
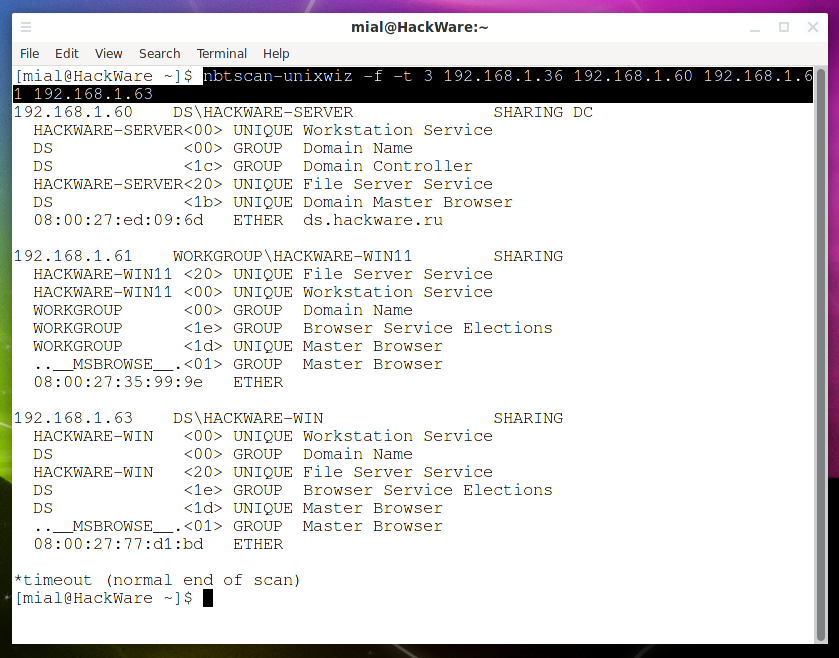
Scan the specified IP addresses (192.168.1.36 192.168.1.60 192.168.1.61 192.168.1.63), display all received information (-f), make 3 attempts per IP address (-t 3):
nbtscan-unixwiz -f -t 3 192.168.1.36 192.168.1.60 192.168.1.61 192.168.1.63
How to install nbtscan-unixwiz
Installation on Kali Linux
The program is pre-installed on Kali Linux. To install in minimal builds run:
sudo apt install nbtscan-unixwiz
Installation on Debian, Linux Mint, Ubuntu
curl --output nbtscan-unixwiz http://unixwiz.net/tools/nbtscan-1.0.35-redhat-linux chmod +x nbtscan-unixwiz sudo mv nbtscan-unixwiz /usr/bin/
Installation on BlackArch
curl --output nbtscan-unixwiz http://unixwiz.net/tools/nbtscan-1.0.35-redhat-linux chmod +x nbtscan-unixwiz sudo mv nbtscan-unixwiz /usr/bin/
Installation on Windows
Go to the official website and download the Windows executable.
nbtscan-unixwiz Screenshots
nbtscan-unixwiz Tutorials
- NetBIOS: what it is, how it works and how to use in information security
- Online service: NetBIOS, SMB (NetBIOS) and Samba (Linux) scanner
Related tools
- NBTscan (100%)
- NetBIOS Share Scanner (100%)
- NMBscan (100%)
- DNSRecon (68.6%)
- mat2 (68.6%)
- Aircrack-ng (Suite of Tools) (RANDOM - 5.7%)
Comments are Closed